"The DOJ, FBI and DOD..., have moved routine communication onto classified networks that are believed not to have been breached, according to two people briefed on the measures. They are assuming that the non-classified networks have been accessed"https://t.co/tbijKoZMW5
— Matt "EINSTEIN, ALBERT FTW" W (@diakopter) December 18, 2020
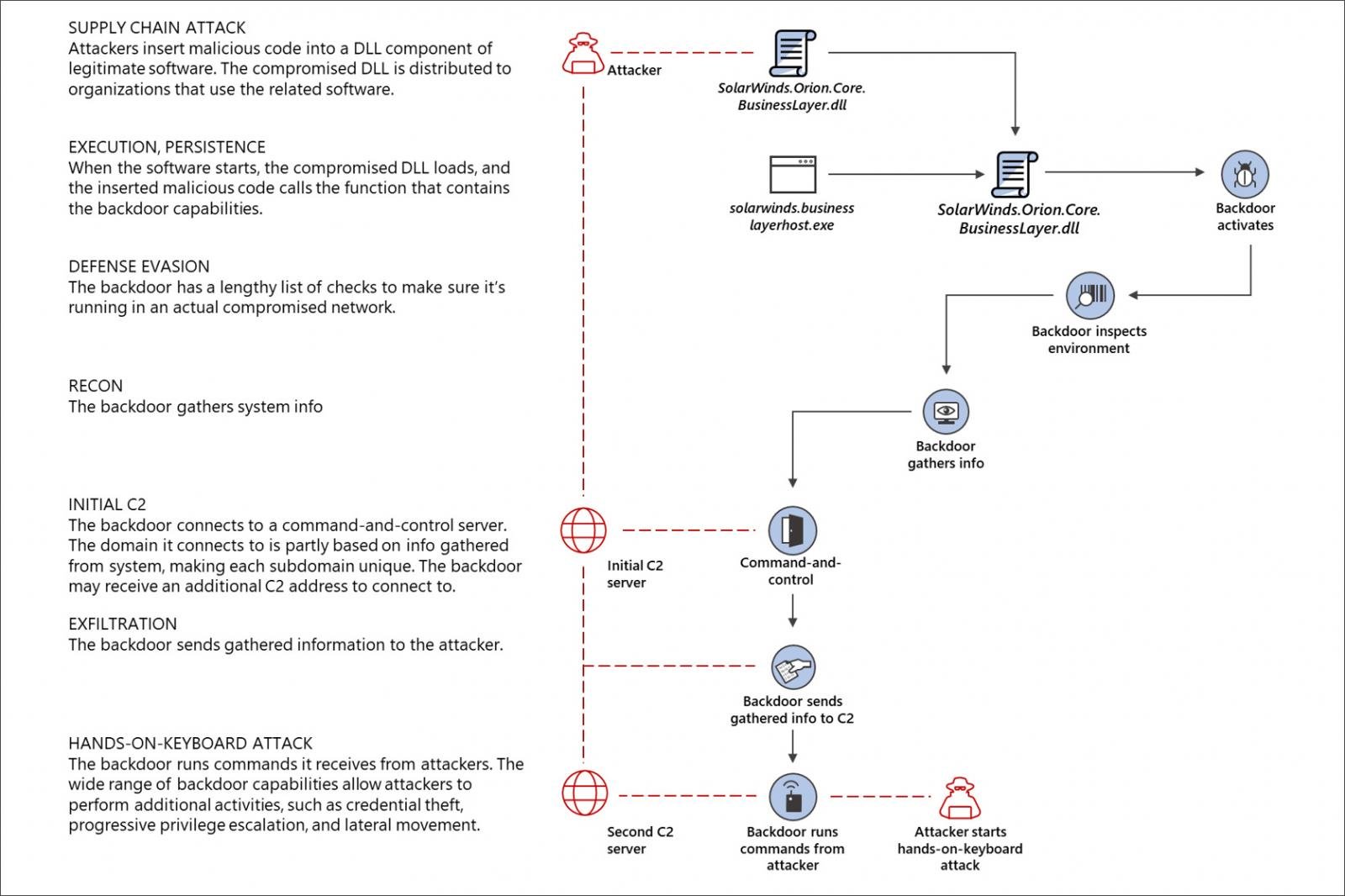
Reason No. 5 gazillion why the SolarWinds hack is so impressive. The hackers had full control of SolarWinds' software build system since October 2019. We know this because the hackers performed a dry run exercise that month. Great reporting by @KimZetter https://t.co/41C3eja90F
— Dan Goodin (@dangoodin001) December 19, 2020
New: SolarWinds hackers did test-run of spy operation in Oct 2019, when malicious SolarWinds files were first downloaded by customers. That version didn't have backdoor in it, however. Indicates hackers were in SolarWinds network in 2019, if not earlier. https://t.co/SuviCKL1GP
— Kim Zetter (@KimZetter) December 18, 2020
“Like other SolarWinds customers, we have been actively looking for indicators of this actor and can confirm that we detected malicious Solar Winds binaries in our environment, which we isolated and removed,” a Microsoft spokesperson saidhttps://t.co/NnWvPFsx3W
— Scott Stedman (@ScottMStedman) December 18, 2020
UK cyber chief says government ‘not hacked’ in SolarWinds operation https://t.co/IUAMWusH2z
— Financial Times (@FT) December 18, 2020
NEW from British security official: Only a “very small” number of British orgs have been compromised by the SolarWinds hack
— Hannah Murphy (@MsHannahMurphy) December 18, 2020
So far none of those identified are UK govt bodies
(NB. the Ministry of Defence & NHS are SolarWinds customers)
w/ @helenwarrell https://t.co/LGuU976MvH
The hack, the victims, and what we know #CyberAttack https://t.co/eYxVeVUnAn
— Bob Carver ✭ (@cybersecboardrm) December 19, 2020
New: SolarWinds hackers did test-run of spy operation in Oct 2019, when malicious SolarWinds files were first downloaded by customers. That version didn't have backdoor in it, however. Indicates hackers were in SolarWinds network in 2019, if not earlier. https://t.co/SuviCKL1GP
— Kim Zetter (@KimZetter) December 18, 2020
Hmm.https://t.co/3z4vQ2Au9B
— Dr. emptywheel (@emptywheel) December 18, 2020
(Kim Zetter is a very good journalist and it confounds me she doesn't have some fancy position.) pic.twitter.com/cPokIC7haa
This is one of those rare instances where *not* immediately applying the latest software patch (as is the norm in many large organizations) was actually a good thing. https://t.co/QkCz9CXIjs via @wired
— ?Crispin Burke? (@CrispinBurke) December 19, 2020
Was Krebs a distant cousin of Maynard G. ??
— Richard Green (@123RHGreen) December 18, 2020
Russia hack claims: What is the Cybersecurity and Infrastructure Security Agency (CISA)? https://t.co/AyqXVwLWGf #FoxNews
Wonder which #Dumbocrat answered the
— Despicable Deplorable Duck #KAG (@DepolableDuck) December 18, 2020
"You need to change your password" email?https://t.co/1ZcB39HQxr
How to Understand the Russia Hack Fallout #cybersecurity #infosec #digitalsecurity https://t.co/YPdcITuuYw
— Kenneth Holley (@kennethholley) December 19, 2020
How to Understand the Russia Hack Fallout #CyberAttack #cybersecurity #security https://t.co/o9JSUVeJR5
— Bob Carver ✭ (@cybersecboardrm) December 19, 2020
Why we should consider Russia’s hacking an act of war https://t.co/4XaJotfaCe
— Benjamin Weinthal (@BenWeinthal) December 18, 2020
Biden isn't even in the White House and they are already trying to start a war with Russia. Setting the stage for a "Sum of All Fears" event.https://t.co/Ks6hoMJRNe
— Steve Svensson (@stompk) December 19, 2020
"Security is not a significant consideration or even well understood."
— Eric Geller (@ericgeller) December 19, 2020
My new story about how the poor state of software security and customers' lack of oversight opened the door to this stunning cyber espionage campaign: https://t.co/MNgvwFrLsJ pic.twitter.com/OtIZ9Jk4C3
How U.S. agencies' trust in untested software opened the door to hackers.
— ?Liz (Lizzy 김혜성) ?? (@zen4ever2us) December 19, 2020
The government doesn’t do much to verify the security of software from private contractors. And that’s how suspected Russian hackers got in.#OnlineSecurity #EveryVoice https://t.co/HwsW2rElK8
Throw UNQUALIFIED , INCOMPETENT TRUMP LOYALISTS , WITH NO EXPERIENCE YOU HAVE A PERFECT
— CeCeIsHappy (@gumboqueen3030) December 19, 2020
HORRIBLE STORM
POLITICO: How U.S. agencies' trust in untested software opened the door to hackers.https://t.co/auTNz6iCKU
How U.S. agencies' trust in untested software opened the door to hackers https://t.co/ozrN250f5P via @politico
— Deborah Blum (@deborahblum) December 19, 2020
How U.S. agencies' trust in untested software opened the door to hackers https://t.co/jZ87NFtT1G by @ericgeller
— hari sreenivasan (@hari) December 19, 2020
The SolarWinds cyberattack: The hack, the victims, and what we know https://t.co/vNtGRtyzpp
— The Cyber Security Hub™ (@TheCyberSecHub) December 19, 2020
"The information is distilled into a format that will hopefully explain the attack, who its victims are, and what we know to this point." #solarwinds #cybersecurity #listiclehttps://t.co/VHHu3ff8ci
— Kayne McGladrey, CISSP (@kaynemcgladrey) December 19, 2020
#Hacking #Solarigate #SolarWinds #Sunburst #SupplyChainAttack #Malware #Vulnerability #CyberCrime #CyberAttack #CyberSecurity
— Richard S. (@Richard_S81) December 19, 2020
The SolarWinds cyberattack: The hack, the victims, and what we know.https://t.co/imN8yReRoQ pic.twitter.com/X9hIE8xocJ
It will take a staggering amount of time to clean up. #treasury #NSA #SolarWindsHack #Orion #infosec #SolarWinds#Microsoft #CyberSecurity #RussianCyberAttack https://t.co/avfQQRXqNl via @wired
— Ralf P. Loserth (@captainsnackbar) December 19, 2020
WHERE’S #TRUMP??? - #Russia hack claims: What is the #Cybersecurity and Infrastructure Security Agency (CISA)?https://t.co/ojvBHvPD9i
— Craig Ahrens (@Craig_Ahrens) December 19, 2020
“How U.S. agencies' trust in untested software opened the door to hackers”
— PierreRochard.com (@pierre_rochard) December 20, 2020
Don’t trust, verify!
Clearly it’s #bitcoin folks that should be regulating the regulators.https://t.co/QmnTwZJMAW
How U.S. agencies' trust in untested software opened the door to hackers. #CyberSecurity #cyberhack https://t.co/DvIbsSONNv pic.twitter.com/AB3AGQdZIB
— Billy Long (@auctnr1) December 20, 2020
"SolarWinds...is one of the most extreme examples of the dysfunction that made this hack possible, but it is far from the only poorly guarded vendor with hooks into the most important computer networks in the world."https://t.co/MNgvwFrLsJ pic.twitter.com/VCm9DuaLsD
— Eric Geller (@ericgeller) December 19, 2020
When testing is not in the news, people think it doesn't matter. But when testing is in the news... https://t.co/YBSnNJzzeA
— James Marcus Bach (@jamesmarcusbach) December 20, 2020
How U.S. agencies' trust in untested software opened the door to hackers [TR: Wrote about security assessments of vendors in my book. I used to work at a security vendor.] #cybersecurity #solarwinds #SolarWindsHack https://t.co/No3K399N7j
— Teri Radichel #cloudsecurity #cybersecurity (@TeriRadichel) December 19, 2020
Untested software left US agencies open to hacking https://t.co/QfY9oerQnf
— Georgia Log Cabin (@GeorgiaLogCabin) December 19, 2020
SolarWinds has 330,000 customers, including:
— Teddy Brosevelt ?? (@_TeddyBrosevelt) December 19, 2020
* Every branch of the Military
* Key Federal agencies
* Major Telecommunications firms
* 80% of the Fortune 500https://t.co/ZkZpfyOGqY
.png)