I have report from Microsoft about SolarWinds hack, including IoCs. Excerpts in this thread: "Microsoft security researchers recently discovered a sophisticated attack where an adversary inserted malicious code into a supply chain development process.... 1/
— Kim Zetter (@KimZetter) December 14, 2020
"The malicious DLL calls out to a remote network infrastructure using the domains https://t.co/c22OWEgB02. to prepare possible second-stage payloads, move laterally in the organization, and compromise or exfiltrate data"
— Kim Zetter (@KimZetter) December 14, 2020
“Power Down.”
— Nicole Perlroth (@nicoleperlroth) December 14, 2020
If you are just joining, USG federal agencies and untold number of SolarWind clients have been compromised via a malicious SolarWinds software update for as long as six months and CISA, the decapitated cyber agency, is telling SolarWinds clients to power it down. https://t.co/Av2uCcrh5f
SolarWinds: "We are recommending you upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible..The latest version is available in the...Customer Portal..An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tues Dec 15" https://t.co/YS3P3HU8Jx
— Kim Zetter (@KimZetter) December 14, 2020
And I mean, literally. Trump went into FBI and DOJ and made sure that everyone with specific expertise in fighting Russia was chased out of there.
— Dr. emptywheel (@emptywheel) December 14, 2020
Welp, Mr. President. They just pwned Treasury. And you not just own that, you invited that.
“The problem is there’s not even been condemnation from the top. President Trump hasn’t wanted to say anything bad to Russia, which only encourages them to act irresponsibly across a wide range of activities.”https://t.co/wodJu5e4SF
— Aaron Rupar (@atrupar) December 14, 2020
If you’re a SolarWinds customer & use the below product, assume compromise and immediately activate your incident response team. Odds are you’re not affected, as this may be a resource intensive hack. Focus on your Crown Jewels. You can manage this. https://t.co/YvSGTv926a https://t.co/WFe89831Dj
— Chris Krebs (@C_C_Krebs) December 13, 2020
This emergency directive reflects how seriously the government considers the threat posed by the suspected Russian hack of SolarWinds. CISA has only issued five emergency directives in its history. https://t.co/mN7ASfiZr0
— Dustin Volz (@dnvolz) December 14, 2020
“We have discovered a global intrusion campaign. We are tracking the actors behind this campaign as UNC2452.” https://t.co/lDDtcqFZqq
— cje (@caseyjohnellis) December 14, 2020
Countermeasures here: https://t.co/BpobQQ7RL8 pic.twitter.com/uE6vttFv5r
SUNBURST malware samples are now available for download, courtesy of @vxundergroundhttps://t.co/nloaipoZY7
— Catalin Cimpanu (@campuscodi) December 14, 2020
Based on what’s coming out it looks like Solarwinds build process was comprised (supply chain attack) and distributed which would mean that potentially other folks that have Solarwinds Orion could have the malicious code as well.
— Dave Kennedy (@HackingDave) December 14, 2020
As @MalwareJake was wise to say anything after this story is speculation. However, I used to run a Managed Service NOC for 40 Colleges using all Solarwinds products. We would talk about how bad it would be if Solarwinds was popped for one school, let alone a supply chain attack. https://t.co/O5XiP3JzhQ
— Ean Meyer: SaaS - Santa as a Service (@EanMeyer) December 14, 2020
Last night we issued an emergency directive to mitigate the compromise involving SolarWinds Orion products: https://t.co/VFZ81W2Ow7. We urge all our partners—in the public & private sectors—to assess their exposure to this compromise and to secure their networks.
— Cybersecurity and Infrastructure Security Agency (@CISAgov) December 14, 2020
According to SolarWinds the vuln the hackers used to breach FireEye and gov agencies appears to be related to an update they made to their software between March and June this year. This suggests the hackers could have been in systems for up to nine months before detection. https://t.co/pBJdOBxHnI
— Kim Zetter (@KimZetter) December 13, 2020
This all happens before an admin even notices the service had an issue.
— Jake Williams (@MalwareJake) December 14, 2020
Even when the NMS is in monitor-only mode, it can still be used to read configurations, which often include enough information for attackers to laterally move to those systems. 8/
TASS is authorised to declare: Russia totally innocent of amazing brilliant hack by very skilled officers who will receive medals.
— thaddeus e. grugq (@thegrugq) December 14, 2020
“Cyberattacks contradict Russia's foreign policy principles,” Russian diplomats lied. https://t.co/3avAC5DbAt
Just imagine, however, if this operation had been Sandworm rather than APT29, and had been focused on disruption instead of espionage: It had the keys to the kingdom across hundreds of US networks through most of this incredibly fraught pandemic/remote work/election year.
— Andy Greenberg (@a_greenberg) December 14, 2020
New: CISA just issued a rare emergency directive instructing federal civilian agencies to review their networks and immediately power down SolarWinds products, saying the hack "poses unacceptable risks to the security of federal networks." https://t.co/l6pC9vwvs6 pic.twitter.com/lHsFpWh5px
— Dustin Volz (@dnvolz) December 14, 2020
This continues to be an interesting development.
— Dave Kennedy (@HackingDave) December 14, 2020
Looks like Solarwinds Orion was the original entry point from the FireEye breach including treasury and commerce.
Microsoft updated 21 hours ago with defender update with artifact detection . https://t.co/rowgktKn2K https://t.co/9dhglscjN9
NMS are excellent targets. They have access to most (often all) systems on the network, so outbound IP ACLs are not a useful control. Netflow usually doesn’t help either since the NMS not only has access to everything, but it’s also talking A LOT. 3/
— Jake Williams (@MalwareJake) December 14, 2020
"This is a much bigger story than one single agency," said one of the people familiar with the matter. "This is a huge cyber espionage campaign targeting the U.S. government and its interests." https://t.co/3exSUSLib9
— Ben Watson (@natsecwatson) December 14, 2020
Hackers reportedly slipped malware into prior SolarWinds software updates, which gave them access to a "God-mode" for infected networks, including the Treasury and Commerce departments.
— Wes Wilson (@weswilson4) December 14, 2020
The Pentagon is also a SolarWinds customer.https://t.co/Srcoztssol https://t.co/OgMhAjJqPx
Our team worked around the clock on this investigation - regularly we hit 18 hour days. I'm proud to have been part of the smartest and most dedicated team I've ever worked with. We had to get creative and fail a lot but when we succeeded we hit big.https://t.co/PKDnd9uEUn
— A little socialism, as a treat (@srunnels) December 14, 2020
.@nakashimae is reporting that Russia's foreign intelligence service, the SVR, is behind these federal agency intrusions: https://t.co/xobSD3OkVB
— Eric Geller (@ericgeller) December 13, 2020
The SVR was also reportedly behind the FireEye hack.
Dear @realDonaldTrump: A reminder below that Russia is not our ally and Vladimir Putin is not your friend. Why are you so scared to condemn Russia or Putin? https://t.co/kZtCYqrsMc
— Ted Lieu (@tedlieu) December 13, 2020
Considerable engineering went in to evading detection, including steganography: “HTTP response bodies attempt to appear like benign XML related to .NET assemblies, but command data…is spread across multiple strings that are disguised as GUID and HEX strings” pic.twitter.com/1HMY0sFcos
— Kenn White (@kennwhite) December 14, 2020
Recall that security also includes availability (CIA triad). The more critical the system, the more likely it is that you want to ensure the availability of it.
— Jake Williams (@MalwareJake) December 14, 2020
NMS ensures availability by monitoring for things like services becoming unresponsive and restarting them. 7/
Common refrain from sources:
— Chris Bing (@Bing_Chris) December 14, 2020
today's news about USG hacks (Commerce + Treasury) and the larger supply chain compromise at Solar Winds, an IT provider for the USG, is "just the tip of the iceberg"
This breach is much worse than it appears atm. And it appears very bad already
Reminder when in July 2017 trump said “Putin and I discussed forming an impenetrable cybersecurity unit so that election hacking, and many other negative things, will be guarded and safe."
— Maggie Jordan (@MaggieJordanACN) December 14, 2020
Fast forward to 2020? https://t.co/ujHOja2F3J
Since earlier in year there has been a serious supply chain attack impacting a very popular enterprise management tool, and multivendor SAML (authentication) attacks allowing for maintained access and data exfiltration.
— Kevin Beaumont (@GossiTheDog) December 14, 2020
IOCs, Azure Sentinel queries etc: https://t.co/8cfUzYVtlP
Why would FireEye have been using third-party remote-access software on its own network? I'm wondering if this may turn out to be two different, but related, attacks. One against gov networks using SolarWind, and a separate attack against FireEye using a different vector. https://t.co/YnBYxlqMwC
— Kim Zetter (@KimZetter) December 14, 2020
New - A review of contract records shows DOD, FBI, DHS, Veterans Affairs and many other U.S. agencies have purchased SolarWinds Orion, the tool used as a launchpad for the huge government and private industry espionage campaign disclosed this weekend.https://t.co/qrxhYHCJDI
— Thomas Brewster (@iblametom) December 14, 2020
And Trump fired Chris Krebs, the head of @CISAgov; great timing: https://t.co/EMelpUD5Eh
— Frank Figliuzzi (@FrankFigliuzzi1) December 14, 2020
Also for those giving @FireEye hell last week and poking fun and jest at their data breach because they were a security company, do you think your threat model would have protected against this?
— Dave Kennedy (@HackingDave) December 14, 2020
Some folks owe some apologies.
If the US government handed you $50m/yr and Presidential authority to address supply chain attacks on US systems, what would you do?
— Matthew Green (@matthew_d_green) December 14, 2020
Full write-up from @FireEye just published, contains TTPs and a lot more detail from the Solarwinds breach:https://t.co/JqS5q9dWNi
— Dave Kennedy (@HackingDave) December 14, 2020
If the Russia connection is confirmed to the US Treasury & Commerce hack it’ll be the most sophisticated known theft of US gov data by Moscow since 2014/15 when Russian intel agencies gained access to WH, State Dept & Joint Chiefs of Staff emails, per NYT https://t.co/1KEDQYEZmd
— Kylie Atwood (@kylieatwood) December 14, 2020
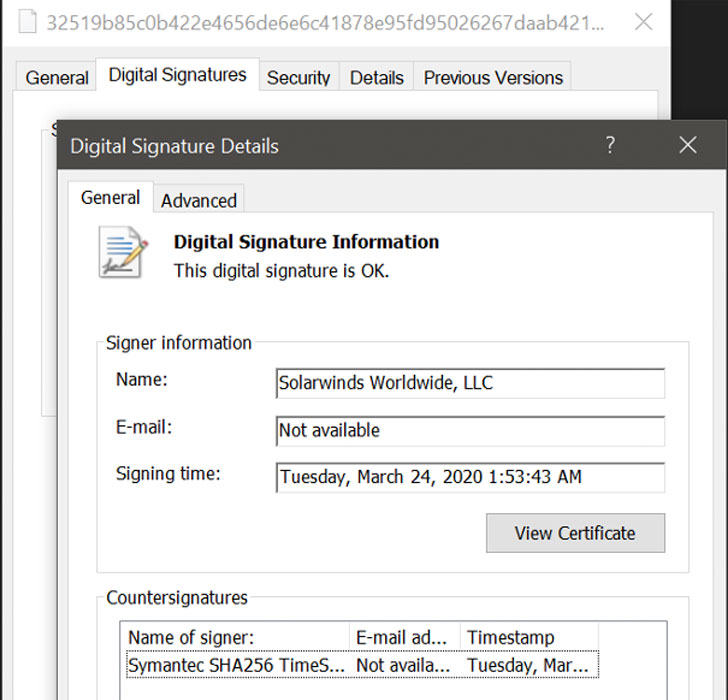
Ok, this gives us a little more info. It was a DLL, as I suggested in a previous tweet, and it occurred in March. https://t.co/2T6yWWMFTU
— Kim Zetter (@KimZetter) December 14, 2020
FireEye has published a blog and a more technical alert on the SolarWinds hack. Links below:https://t.co/0VNMW21nSbhttps://t.co/rXv8xBDHGG
— Dustin Volz (@dnvolz) December 14, 2020
Anyone who uses Orion Monitoring products and want to walk me through what they are and what they do? https://t.co/fXQqxbU3YC
— Raphael Satter (@razhael) December 13, 2020
FireEye is likely breathing a bit of a sigh of relief given the news tonight. They can say they went public with this widespread supply-chain attack first, which likely helped alert other victims inside and outside government of a potential Russian intrusion into their systems.
— Dustin Volz (@dnvolz) December 14, 2020
Outstanding reporting from @nakashimae (following up on @Bing_Chris who broke the story) of the breach at Treasury.
— Jake Williams (@MalwareJake) December 13, 2020
WAPO is saying that attackers used SolarWinds in the breach. It’s a good reminder to check the access your network management software has.https://t.co/G1U9AnXAJX
More disclosure on FireEye/SolarWinds attack chain. Fascinating attack vector - stealing the certificate that signs SAML login tokens lets you just impersonate and include any claims you want https://t.co/k8xn9fcmvQ
— SwiftOnSecurity (@SwiftOnSecurity) December 14, 2020
Just released by FireEye, confirming signed updates from SolarWinds enterprise monitoring software were backdoored. This is the real deal folks.https://t.co/R6LlsmaWD1 pic.twitter.com/p99Crw2SvL
— Kenn White (@kennwhite) December 14, 2020
NMS are usually used to monitor network devices and critical servers. If you’ve ever seen a network map with devices shown as green/yellow/red, that was probably built by an NMS.
— Jake Williams (@MalwareJake) December 14, 2020
How does the NMS generate the map? Sometimes it’s as simple as a ping command. 4/
There it is - @CISAgov issues Emergency Directive 21-10, directing Fed civilian agencies to take action on SolarWinds compromise. Still digesting, but this is a strong move. Proud of the team. Everyone else should refer to this as they chart next steps. https://t.co/DIz9EZkc1V
— Chris Krebs (@C_C_Krebs) December 14, 2020
Just got this from @solarwinds:https://t.co/30EClmPXqw pic.twitter.com/1yjYp6lUyf
— Raphael Satter (@razhael) December 13, 2020
Confirming this bit of reporting, Solar Winds is patient zero, per two sources familiar:https://t.co/wcxDuDYKjP
— Chris Bing (@Bing_Chris) December 13, 2020
Will Trump say anything against Putin?
— Wajahat "Wears a Mask Because of a Pandemic" Ali (@WajahatAli) December 13, 2020
How will Republicans respond?
Russian Hackers Broke Into Federal Agencies, U.S. Officials Suspect https://t.co/LoCy3stTDa
The SolarWinds hack is global and widespread. A source said FireEye has seen customers compromised in North America, Europe, Asia and the Middle East and across a range of sectors including telecom, tech, health care, automotive, energy and government. https://t.co/l6pC9vwvs6
— Dustin Volz (@dnvolz) December 14, 2020
More often, the NMS uses SNMP (network management protocol) or an installed agent to learn the status of remote devices.
— Jake Williams (@MalwareJake) December 14, 2020
Now they’re called network MANAGEMENT systems for a reason: in addition to status, they can modify configuration, restart services, etc. 5/
Excellent thread on the USG hacks: https://t.co/B3ovVPsP46
— Zack Whittaker (@zackwhittaker) December 14, 2020
Good find - the vuln discovered in the SolarWinds system that resulted in a June patch. Was this the patch SolarWinds was referring to when it said an update it made to its software between March-June may have introduced a new vuln the Russians exploited? https://t.co/j1kjNlA3ls https://t.co/bu8Lxe6EUA
— Kim Zetter (@KimZetter) December 14, 2020
Supply chain attacks are absolutely some of the most devasting type of compromises we see.
— Dave Kennedy (@HackingDave) December 14, 2020
Any organization running that software could be impacted and selected as a target.
This group chose well, Solarwinds is used heavily around the globe.
SOLARWINDS in statement said it is aware of a potential vulnerability related to updates of its Orion technology management software that were released between March and June of this year.
— Dustin Volz (@dnvolz) December 13, 2020
FireEye has also released a technical breakdown of the malware used in the attacks, which they named SUNBURST: https://t.co/O97ovOUam3
— Catalin Cimpanu (@campuscodi) December 14, 2020
Countermeasures/detection rules are here: https://t.co/g2QWzbeugF pic.twitter.com/aPsomMLYZS
Okay folks, let’s talk about SolarWinds.
— Jake Williams (@MalwareJake) December 14, 2020
For those not familiar with it, SolarWinds is a network management system (NMS). It’s probably the most ubiquitous NMS out there, so we shouldn’t jump to conclusions that FireEye and Treasury were both breached by an SolarWinds vuln. 1/
UPDATE: Sources tell me that the victims--Treasury, Commerce, FireEye--were breached through an IT Management System called Solar Winds https://t.co/DDnvtFo0uG
— Ellen Nakashima (@nakashimae) December 13, 2020
Is this part of his declared declassification strategy? https://t.co/yirgtN51Kw
— Matt (@mattk) December 14, 2020
For more information about the global software supply chain threat we identified, please read our blog post. https://t.co/2MvzLnjKZ0
— FireEye (@FireEye) December 14, 2020
Russia has hacked several govt agencies including Treasury and Commerce as part of a widespread attack that also hit FireEye. They got in through a flaw in IT firm SolarWinds, which has 100s of thousands of customers, including military and Fortune 500.https://t.co/l6pC9vwvs6
— Dustin Volz (@dnvolz) December 13, 2020
3/ @solarwinds has issued a statement confirming their products have contained the backdoor since March: https://t.co/LTv9BPgtqd
— Aziz Gilani (@TexasVC) December 14, 2020
It's kind of wild this hacking campaign went undetected for months and then it hit FireEye and then everyone could see it. Big flex and poor targeting choice?
— Chris Bing (@Bing_Chris) December 13, 2020
.@nakashimae pushing reporting further. Seems that APT29/Russian intel SVR is behind it: https://t.co/V2rNEtfSDE
— Chris Bing (@Bing_Chris) December 13, 2020
Microsoft says that their earliest IOC for the Solarwind breach is March 2020. pic.twitter.com/Qf6lwltKRe
— Jerry Gamblin (@JGamblin) December 14, 2020
Key question, if Solar Winds is vulnerable... where else in the massive customer list has APT 29 been? https://t.co/atD2FY8GVl pic.twitter.com/KhYs4oXSdt
— John Scott-Railton (@jsrailton) December 13, 2020
Some other thoughts on this #SolarWinds supply chain hack.
— Dmitri Alperovitch (@DAlperovitch) December 14, 2020
We don’t yet know if every customer of SolarWinds who is autoupdating is compromised (likely not given the overall stealthiness of the intrusions to date - adversary most likely down selected to targets of interest) 1/
Sweet jeebus, software "supply chain attack". This is red-alert time. https://t.co/EitQ2Y4VEW
— Nicholas Weaver (@ncweaver) December 14, 2020
Wow, this SolarWinds hack was high-end. Lots of moving parts; long reconnaissance stage; very targeted; silent deplot; delay-before-execute; context-specific exfil to keep quiet; very professionally put together. Serious kudos to the folks who caught it. https://t.co/kYvJFrvRht
— Pwn All The Things (@pwnallthethings) December 14, 2020
Solar Winds' other government customers, per its website: Census Bureau, DOJ, Oak Ridge and Sandia National Labs, VA, Army, Air Force, Navy, and Marine Corps. https://t.co/NKIKB1elFS
— Eric Geller (@ericgeller) December 13, 2020
Plus state, local, educational, and foreign customers, e.g. Texas, NHS, and European Parliament. https://t.co/sZ6ggvUd1n
SolarWinds has also published a security advisory:
— Catalin Cimpanu (@campuscodi) December 14, 2020
-SolarWinds Orion versions 2019.4 through 2020.2.1, released between March 2020 and June 2020, are believed to have been compromised
-Company plans to release an update this week to remove the malwarehttps://t.co/fws5UVR1WB pic.twitter.com/r1Bf6bwnc4
Seems like a bad time to have fired the CISA Director. https://t.co/fG56KzDa2m
— Mike Masnick (@mmasnick) December 13, 2020
This is explains the wide spread hack operation. Why hack one by one, while you can just tweak the code of server tools made by solarwinds while in development, and widely used by government agencies and the private sector. That is fucking smart https://t.co/RbuZ52mmqx
— ALT-immigration ? (@ALT_uscis) December 14, 2020
Struck by fact that for 6 weeks now @realDonaldTrump and 100+ Republican members of Congress have been talking about a hack that never happened - of the vote. Total silence on the one that did happen: Russian hackers inside the Fed. govt.'s own agencies. https://t.co/yQywoSUIHp
— David Sanger (@SangerNYT) December 14, 2020
BUT here is the good news - no adversary has enough human resources to effectively exploit every potential victim. They pretty much HAVE to focus on those they care most about.
— Dmitri Alperovitch (@DAlperovitch) December 14, 2020
But no doubt this is squarely in the #goodproblemtohave department for them. Very impressive op 2/2
Anybody else old enough to remember “remote IT administration or monitoring tools” were handy hacking tools & were called “Back Orifice”?
— Katie Moussouris (she/her) is getting vaccinated (@k8em0) December 13, 2020
So when a product has this description, it has access by def.
If there’s a security hole in it, or it’s taken over by criminals, you’re sunk. https://t.co/X9tkIhr2zq
It never gets old or any less absurd to recall that Trump wanted to have a joint cyber unit with Putin.
— Bianna Golodryga (@biannagolodryga) December 13, 2020
https://t.co/P6QVMEUW63
Great writeup from @FireEye on the #SolarWinds supply chain hack. Really good tradecraft by the adversaryhttps://t.co/fyorfmQCuI pic.twitter.com/DCXQeUEGzJ
— Dmitri Alperovitch (@DAlperovitch) December 14, 2020
SolarWinds is used by hundreds of thousands of organizations... And it has admin access to the network. Monday may be a bad day for lots of security teams. #2020awesomenesscontinues https://t.co/ss4swwW40s
— Dmitri Alperovitch (@DAlperovitch) December 13, 2020
.@CISAgov has issued an emergency directive on actions that gov agencies need to take immediately to mitigate against the SolarWinds threat: https://t.co/WoiLDTCUXu pic.twitter.com/pKdCGr1OK5
— Kim Zetter (@KimZetter) December 14, 2020
"we do not know how the backdoor code made it into the library..research indicates...the attackers might have compromised internal build or distribution systems of SolarWinds, embedding backdoor..into a legitimate SolarWinds library" - SolarWinds.Orion.Core.BusinessLayer.dll 4/
— Kim Zetter (@KimZetter) December 14, 2020
It will be interesting to get details on this. If its a security flaw in Solar Winds then many others are at risk.
— BrianHonan #BLM He/Him (@BrianHonan) December 14, 2020
Also, a reminder that all remote management tools while providing benefits are also a useful vector for attackers to use https://t.co/7VKrnIvrOr
That would be an illusory correlation. If you’re jumping to that conclusion (or that FireEye and Treasury use a common MSP), at least be clear that you’re guessing.
— Jake Williams (@MalwareJake) December 14, 2020
It’s a lot like the DC Sniper case where we focused on white vans. SolarWinds (like white vans) is everywhere 2/
"This attack was discovered as part of an ongoing investigation" 3/ pic.twitter.com/Iq8FxPpnNH
— Kim Zetter (@KimZetter) December 14, 2020
BREAKING: Russian government spies are behind a broad hacking campaign that has breached U.S. agencies and a top cyber firm https://t.co/DDnvtFo0uG
— Ellen Nakashima (@nakashimae) December 13, 2020
This is potentially a hugely consequential hack. SolarWinds' customers include over 425 of US Fortune 500, all branches of military, the NSA, State, Office of the President, top US accounting firms, defense titans like Lockheed, hundreds of universities.https://t.co/rUpWQXKn4v https://t.co/LBxHod3NYk
— Dustin Volz (@dnvolz) December 13, 2020
Relieved that next month we can finally have the head of our government do what cybersecurity professionals have been calling for for years. Attribution and Consequences. https://t.co/Nbjh11UNZT
— Elizabeth Neumann (@NeuSummits) December 14, 2020
NEWS
— Yashar Ali ? (@yashar) December 13, 2020
The Trump administration acknowledged on Sunday that hackers acting on behalf of a foreign government — almost certainly a Russian intelligence agency — broke into a range of key government networks and had free access to their email systems. https://t.co/4JgigdpXAt
Not all NMS are able to change anything, and those that can don’t always allow it for all systems on the network.
— Jake Williams (@MalwareJake) December 14, 2020
The bad news is that the most critical systems are also those most likely to have change access through NMS configured. This isn’t a failure in security modeling. 6/
I have a one-word suggestion that Trump will ignore but Biden will hopefully heed: CONSEQUENCES.
— Miles Taylor (@MilesTaylorUSA) December 14, 2020
The days of Russia “getting away with it” are over. https://t.co/MIJnYsH6mj
This walks through everything pretty clearly as far as mode and method.
— JohnMB | CyberInsight on YouTube (@JBizzle703) December 14, 2020
Good time to start looking for outbound traffic to avsvmcloud(.)com for beaconing. https://t.co/fsmsyvl4nZ
Remember when Trump announced a joint US-Russian cyber security service?
— Grant Stern (@grantstern) December 13, 2020
https://t.co/H4YkzKzP1s
Microsoft has published a report on the hacking campaign that has breached several federal agencies. It confirms that the intruders used SolarWinds product vulnerabilities for initial access and then forged authentication tokens to spread further. https://t.co/pSjbo5qimX
— Eric Geller (@ericgeller) December 14, 2020
I'm already pissed off that I'm going to hear "But what about SolarWind?" from some wiseass every time I tell people to take their security updates for the next several years.
— Eva (@evacide) December 14, 2020
If this started in March they’ve had almost 200 years on those networks!! ? https://t.co/3CQEk3uo9X
— thaddeus e. grugq (@thegrugq) December 14, 2020
Incident comes shortly after Trump administration fired heads of DHS' Cybersecurity Infrastructure Protection Agency. There is also no current top cyber official.
— Chris Bing (@Bing_Chris) December 13, 2020
Multiple agencies wrapped up in the investigation.
Keep an eye on story (updating): https://t.co/r5BN9gxumC
“At Commerce, the Russians targeted the National Telecommunications and Information Administration, an agency that handles internet and telecommunications policy” -Russian government spies are behind a broad hacking campaign that has breached U.S. agencies https://t.co/71zyv9wXn6
— Clint Watts (@selectedwisdom) December 13, 2020
Some here pointing to the SolarWinds hack as the other Sandworm/NotPetya shoe dropping. Still early, but this looks like targeted spying as you'd expect from APT29/SVR, not Sandworm/GRU-style disruption. Not yet sure it's less serious, just very different. https://t.co/2MwIRsmprT
— Andy Greenberg (@a_greenberg) December 14, 2020
"A malicious software class was included among many other legitimate classes and then signed with a legitimate certificate. The resulting binary included a backdoor and was then discreetly distributed into targeted organizations.... 2/
— Kim Zetter (@KimZetter) December 14, 2020
Microsoft has also added detection rules to Defender. Company calls the malware Solarigate.https://t.co/Q3397Y5Cx6 pic.twitter.com/nIIt5uDOXl
— Catalin Cimpanu (@campuscodi) December 14, 2020
.@CISAgov encourages organizations that use SolarWinds Orion Platform software to review the following advisories for information on publicly identified nation state backed threat actor activity:https://t.co/zcAREzsbAXhttps://t.co/EvIwOsUusVhttps://t.co/fs5Cn40WAI
— US-CERT (@USCERT_gov) December 14, 2020
And their security advisory site https://t.co/BEYk20FUkJ
— We The Inevitable (@WeTheInevitable) December 14, 2020
SolarWinds: "We are recommending you upgrade to Orion Platform version 2020.2.1 HF 1 as soon as possible..The latest version is available in the...Customer Portal..An additional hotfix release, 2020.2.1 HF 2 is anticipated to be made available Tues Dec 15" https://t.co/YS3P3HU8Jx
— Kim Zetter (@KimZetter) December 14, 2020
.@SolarWinds supply chain attack #evilgrade@FireEye Security Breach
— Francisco Müller Amato (@famato) December 14, 2020
Total: 1688
Source: @shodanhqhttps://t.co/e0ZXkCys38
Hotfix Orion Platform version 2020.2.1 HF 1
More information is available at https://t.co/VeE1a1E5WE
/cc @campuscodi @faradaysec pic.twitter.com/ghplRGdvmR
Some other big companies round the place yah use Solarwinds also...hope they taking note...????https://t.co/T6mQywrlQ2
— Mr Open Source (@trevorforrest) December 14, 2020
"RT @TheHackersNews: ⚠️URGENT⚠️
— President-Elect ❤?? Trip Elix ? ?❤ (@trip_elix) December 14, 2020
Hackers exploit #Solorigate supply-chain backdoor in #SolarWinds enterprise monitoring software to breach US Treasury, Commerce Department, other government agencies, and cybersecurity firm #FireEye.
Details: https://t.co/21N8Z0SO9T#infosec #…
⚠️ @CISAgov issued an Emergency Directive calling on all federal civilian agencies to take immediate action to secure their networks & mitigate the compromise involving SolarWinds Orion products: https://t.co/rmn9CyD0Qx#InfoSec #InfoSecurity #InformationSecurity #NetSec pic.twitter.com/san0bO17Xy
— Cybersecurity (@cyber) December 14, 2020
JUST RELEASED: Emergency Directive 21-01 calls on all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately. Read more: https://t.co/VFZ81W2Ow7
— Cybersecurity and Infrastructure Security Agency (@CISAgov) December 14, 2020
FLASH: "Emergency Directive 21-01 calls on all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately."-@CISAgov Read more: https://t.co/002Xaf6SV8
— John Basham ?? (@JohnBasham) December 14, 2020
THERE WAS ELECTl0N lNTERFERENCEhttps://t.co/BfZk6jPYVV
— We The Inevitable (@WeTheInevitable) December 14, 2020
CISA Issues Emergency Directive to Mitigate the Compromise of Solarwinds Orion Network Management Products
Last night we issued an emergency directive to mitigate the compromise involving SolarWinds Orion products: https://t.co/VFZ81W2Ow7. We urge all our partners—in the public & private sectors—to assess their exposure to this compromise and to secure their networks.
— Cybersecurity and Infrastructure Security Agency (@CISAgov) December 14, 2020
Just summarized some thoughts, even though we still lack many details. Everything isn't doom and gloom. At least, yet.https://t.co/TPl1VHp3bF
— Lesley Carhart (@hacks4pancakes) December 14, 2020
please read our comprehensive blog on #UNC2452 and the #SUNBURST backdoor https://t.co/SU7hPkn4BL
— Van (@Wanna_VanTa) December 14, 2020
This is a fantastic IOC from @FireEye in the #SolarWinds malware payload. Most networks don't have much PUT activity going on (though seeing it might be something else entirely given TLS).https://t.co/2ouEaTOjBW pic.twitter.com/9FN0oZJE2B
— Jake Williams (@MalwareJake) December 14, 2020
A few hours ago @FireEye has published a very well documented article on the Solarwinds supply chain compromise.https://t.co/mkklo6OPer
— Olaf Hartong (@olafhartong) December 14, 2020
I've converted their indicator share into KQL hunting querieshttps://t.co/pEKtJYzbvj#SUNBURST #MDE #ThreatHunting
Okay more details from FireEye, it did rely on default outbound network access, but they went to incredible lengths to cloak it. This is top tier effort stuff god damn.https://t.co/G8CdgiowIA pic.twitter.com/TguDZcUooP
— SwiftOnSecurity (@SwiftOnSecurity) December 14, 2020
So you want to talk about the massive software supply chain intrusion & the most carefully-planned, complex espionage I’ve ever helped uncover?
— Nick Carr (@ItsReallyNick) December 14, 2020
Start here: https://t.co/m1nJG5UlVk ?
But then what?? Let’s talk about some post-compromise techniques...
Most of these IP addresses are private/non-routable. But those highlighted? They belong to Microsoft. The #SolarWinds attackers REALLY didn't want their malware running there.
— Jake Williams (@MalwareJake) December 14, 2020
If you work in @msftsecurity, give yourselves a pat on the back. You earned it.https://t.co/2ouEaTOjBW pic.twitter.com/yPQJHSJFsN
Solar Winds Softwarehttps://t.co/3a5BSXSDjThttps://t.co/apLU15BtPl pic.twitter.com/jT5BkfTkpG
— We The Inevitable (@WeTheInevitable) December 14, 2020
Yeah that's pretty much exactly what happened combined with a boatload of 0days and novel tooling. The write-up on the malware and MO is really interesting if you haven't read it yet. https://t.co/8GPkptom2T
— Andrew W. (@Zonr0) December 14, 2020
Confirming earlier suspicions, FireEye says that its breach was part of a global campaign of cyberattacks leveraging a compromised SolarWinds Orion software update.
— Eric Geller (@ericgeller) December 14, 2020
FireEye is notifying victims it discovers.https://t.co/A0Tg0hkXFi
Technical details: https://t.co/ddDPPXKSVw pic.twitter.com/8cvMv3ENya
Hot ? #threatintel from @FireEye. #UNC2452's ?#SUNBURST? is the backdoor that was found inside of trojanized #SolarWinds software. Cancel your holiday plans. I know you already bought and opened your presents anyways. Early gift from the team: https://t.co/kA4KxwOyki
— Andrew (@anthomsec) December 14, 2020
Microsoft is referring to it as #Solorigate
— christmas2016_passwords.xlsm (@da_667) December 14, 2020
While FireEye is referring to it as #SUNBURST
looks like FEYE has an ioc repo.https://t.co/NBLBmJHIUE
and blog post.https://t.co/LMy2EelGR7
and it looks like @jfslowik has done some passiveDNS pivoting.https://t.co/81khhFh9cU
???? Hats off to the entire Mandiant/FireEye team for the immense effort that went into discovering this. A true masterclass in detecting what has been the most evasive threat actor I've had a part in investigating.https://t.co/CzLIdfvm8C
— Doug Bienstock (@doughsec) December 14, 2020
Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor
— ? SITTING BULL? (@X16Eagle) December 14, 2020
December 13, 2020 https://t.co/35lXxhtxxc
Details on the SolarWinds supply chain attacks. https://t.co/HNBlZKWojI
— John Hultquist (@JohnHultquist) December 14, 2020
If you are new or wanting to get into infosec, the case study of the year (if not decade) is unraveling right now. Read up, take notes, and ask questions.https://t.co/dbnUSpzEUT
— Matt Bromiley ?? (@_bromiley) December 14, 2020
Good folks will become better defenders and hunters because of this.
Here is FireEye's report on the SolarWind hack, published today. They're calling the threat SUNBURST: https://t.co/bp2BES73XU
— Kim Zetter (@KimZetter) December 14, 2020
There it is - @CISAgov issues Emergency Directive 21-10, directing Fed civilian agencies to take action on SolarWinds compromise. Still digesting, but this is a strong move. Proud of the team. Everyone else should refer to this as they chart next steps. https://t.co/DIz9EZkc1V
— Chris Krebs (@C_C_Krebs) December 14, 2020
? CISA has issued an emergency order requiring federal agencies to disable SolarWinds IT products, which hackers exploited to penetrate Treasury, NTIA, and possibly other agencies. https://t.co/vYzGdtH4uI
— Eric Geller (@ericgeller) December 14, 2020
Disconnection "is the only known mitigation measure currently available."
Update on the hack. Public informationhttps://t.co/4T1F82YIW8
— Noble Dave, #StopTheSteal.US ??? (@DaveVino) December 14, 2020
The US cyber agency issued an emergency directive ordering federal agencies to disconnect SolarWinds' products: https://t.co/s7nEog1MAS
— Hannah Murphy (@MsHannahMurphy) December 14, 2020
SolarWinds' client list also includes UK defence agencies, the NHS, the European Parliament, plus US govt & military: https://t.co/lcADiOrlcC
New from @CISAgov in relation to Russia hacking of Treasury & Commerce https://t.co/pMeWf6stor - Emergency Directive 21-01 https://t.co/0d7oOSoevg
— Clint Watts (@selectedwisdom) December 14, 2020
“The compromise of SolarWinds’ Orion Network Management Products poses unacceptable risks to the security of federal networks,” said CISA Acting Director Brandon Wales. | Mitigate SolarWinds Orion Code Compromise (CISA): https://t.co/C0QfqteeQY
— 780th Military Intelligence Brigade (Cyber) (@780thC) December 14, 2020
U.S. government agencies were hit by a widespread campaign of cyber-attacks https://t.co/8YJaPjJ3Mr via @technology
— Dr. Jeffrey Guterman (@JeffreyGuterman) December 14, 2020
U.S. government agencies were hit by a widespread campaign of cyber-attacks that may eventually rank as among the worst in recent memory, sources say https://t.co/ZeZd8jpf48 pic.twitter.com/D2A04LNYRJ
— Stuart Wallace (@StuartLWallace) December 14, 2020
Bet me .#Fuckolini knew all
— Vince Olson , Councilman & EMT of Big Water , Utah (@SteelToeTruth) December 14, 2020
about this .https://t.co/26dgyllhCR
A huge breach of a database of nearly 2 million CCP spy operatives all over the world is leaked today... so what is reported on?
— Sir Lord Travis Wright I, Esq. (@teedubya) December 13, 2020
The "Russians" hacking the US Treasury. LOL. It's almost predictable at this point. https://t.co/5E8c9CdfWz
Suspected Russian hackers spied on U.S. Treasury emails
— LiA (@LibsInAmerica) December 13, 2020
Trump is handing them all our national security secrets on a platter. https://t.co/9AfBOKyFFt
Reminder as news comes in regarding Russia hacking into the Treasury Department, Commerce's NTIA & other USG agencies...
— Maggie Jordan (@MaggieJordanACN) December 13, 2020
Trump recently fired the head of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, @C_C_Krebs.https://t.co/pSfYYItIRk
Hackers spied on U.S. Treasury emails for a foreign government
— Michael O'Grady (@mog7546) December 13, 2020
The breach presents a major challenge to the incoming administration of #Biden as officials investigate what information was stolen and try to ascertain what it will be used for#MOG https://t.co/zusHxX44Zq
US Finanzministerium wurde gehackt. Daten wurden gestohlen.
— Frau Nulleberg (Autobahnaktivisten Account) (@nulleberg) December 13, 2020
Nationaler Sicherheitsrat tagt.
„The hack is so serious it led to a National Security Council meeting at the White House on Saturday, said one of the people familiar with the matter.“ https://t.co/d1r58NCx8y
Seems very coincidental that right after the #FireEyeHack the federal government is hacked.https://t.co/338x9nM6su
— No lives matter till black lives do (@TrumpResign) December 13, 2020
I hope they didn't steal all our Fedcoins!
— Dr. Rudy Havenstein, MPLA, UDA, IRA, UK. (@RudyHavenstein) December 13, 2020
https://t.co/bkLVmIgxjp
Suspected Russian hackers spied on U.S. Treasury emails - sources https://t.co/phlCz4JHDd #SmartNews
— Temptingfate?? (@temptingfate7) December 13, 2020
@RepJohnKatko isn’t this supposed to be your area????
— Steve Skinner (@oswegos1) December 13, 2020
Exclusive: Hackers spied on U.S. Treasury emails for a foreign government - sources #SmartNews https://t.co/O1T3wdIggs
"“I’m sure that the departments like NSA and Cyber Command are coming up with options, that the Treasury Department is looking at sanction options, that the State Department is looking for how they will send a strong signal,” Spaulding said."https://t.co/cjOHTq0BXm
— Justin "Rabbit Hole J. Cole" Coleman (@DemopJ) December 15, 2020
Trump dropped our defenses on purpose.
— Justice4all (@JamesLindholm1) December 14, 2020
Aid and comfort to our enemy
How much vital crucial secret did Russians get??
If American men and women in armed forces are hurt.
Trump should be righteously
Charged and jailedhttps://t.co/fglHWaOTQs
?????????
— Andrew C ™️ PRESIDENT ELECT (@Sheckyi) December 14, 2020
Swalwell, Schiff, Nadler, Pelosi, Cryin’ Chuck and the rest of you American hating “sons of bitches” look what you let happen....
US agencies hacked in monthslong global cyberspying campaign https://t.co/wOekTpFm7e
SolarWindsのネットワーク管理製品を高度なサプライチェーン攻撃でトロイの木馬化させて、それを通じて米政府機関への諜報戦?厄介ですね。SolarWindsは顧客に製品の更新を呼びかけ。https://t.co/n1UZ4nQP6m / “米財務省や商務省に大規模サイバー攻撃 背後にロシア政府か…” https://t.co/SlMU0CNXtX
— 上原 哲太郎/Tetsu. Uehara (@tetsutalow) December 15, 2020
? #SolarWinds is advising it’s Orion customers to take the following steps regarding their use of the @solarwinds Orion Platform. Link to advisory: https://t.co/9eK2dkB5MR
— Mark Lynd ?CISSP ISSMP ISSMP (@mclynd) December 14, 2020
Here is an article with more detailed information on the hack: https://t.co/oRNsJ53702#Cybersecurity pic.twitter.com/UlCU0tQsp0
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor #Cybersecurity #security https://t.co/b6kmd1oNDT
— Bob Carver ✭ (@cybersecboardrm) December 14, 2020
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor #Cybersecurity #cyberattack #security https://t.co/ZIIMwBT5Ci
— Bob Carver ✭ (@cybersecboardrm) December 14, 2020
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor #Cybersecurity #security https://t.co/B4ajTbtbFz
— Bob Carver ✭ (@cybersecboardrm) December 14, 2020
US Agencies and FireEye Hacked Using SolarWinds Software Backdoor https://t.co/rH6trLkszg << Potentially a huge #cybersecurity incident. Look at customer list using Orion: The NHS were using it in 2017 (https://t.co/ylOy8oWaEi ) , US Treasury and Department of Commerce. #infosec pic.twitter.com/RorEbM0VgN
— Jen Stirrup #Leadership #WomenInTech #Diversity (@jenstirrup) December 14, 2020
US Agencies and FireEye Were Hacked Using SolarWinds Software Backdoor#cybersecurity #datasecurity #dataprotection #databreach #backdoor #cyberespionage https://t.co/4pF7Em5Z44
— 4Securitas Team (@4securitasTeam) December 15, 2020
One of the biggest hacks in history. The FireEye breach is much bigger than we thought. Solarwinds software used in supply chain attack targeting US govt agencies critical orgs. https://t.co/i88nesmVnt
— Fabio Viggiani (@fabio_viggiani) December 14, 2020
US treasury and commerce departments targeted in cyber attack.
— Fabrizio Bustamante (@Fabriziobustama) December 15, 2020
By @BBC #CyberSecurity #Cyberattacks #Tech #infosec
Cc: @Nicochan33 @archonsec @AudreyDesisto @JBarbosaPR @missdkingsbury @mclynd @todddlyle @avrohomg @gvalan @fogle_shane @AghiathChbibhttps://t.co/3ai2gxERuD pic.twitter.com/DKwKSgMOFX
The #US #treasury and #commerce #departments
— Spiros Margaris (@SpirosMargaris) December 14, 2020
targeted in #cyberattack https://t.co/jW5u12fBsK #fintech #CyberSecurity @BBCNews pic.twitter.com/PobOPcaXKA
#BREAKING: FROM CISA DIRECTLY - this will give @realDonaldTrump EMERGENCY POWERS PER 2018 EXECUTIVE ORDER. IT HAS STARTED JUST AS WE ANNOUNCED IT WOULD. #RigForRed #MilitaryTribunals https://t.co/EcYg9Zg5Ge
— America First (@AmericaFirst_DT) December 14, 2020
Emergency Directive 21-01 calls on all federal civilian agencies to review their networks for indicators of compromise and disconnect or power down SolarWinds Orion products immediately.https://t.co/aRrGE2afVs pic.twitter.com/ICZFWJp30f
— ⚔️??Bad Kitty 真相 ? ?⚔️ (@pepesgrandma) December 14, 2020
Federal civilian agencies must take action on a known compromise involving SolarWinds Orion products that is being exploited by malicious actors: https://t.co/VFZ81W2Ow7
— Cybersecurity and Infrastructure Security Agency (@CISAgov) December 15, 2020
We recommend all organizations review Emergency Directive 21-01 & take steps to secure their networks. pic.twitter.com/dHfZaOh3Qf
Here’s my blog where I talk about the least sexy and marketable things you can do right now https://t.co/TPl1VHp3bF
— Lesley Carhart (@hacks4pancakes) December 14, 2020
This incident should be treated as serious and stakeholders should take immediate action. For indicators of compromise and how to #detect the #sunburst malware, visit the @FireEye blog: https://t.co/v5uZcVRp4f https://t.co/0rxuhQvifI
— NSA Cyber (@NSACyber) December 14, 2020
The attackers have compromised signed libraries that used the target companies’ own digital certificates, attempting to evade application control technologies. #APT #SolarWinds
— blackorbird (@blackorbird) December 14, 2020
msrc:https://t.co/JSmyKMXpLu
link:https://t.co/vDuoXUVunv pic.twitter.com/tHPzVSjVd0
A thread of all the useful #SUNBURST / #SolarWinds links so far.
— blueteamblog (@blueteamblog) December 15, 2020
https://t.co/Vae7HpsDTA - FireEye Blog on Incident https://t.co/eBnAaRvXek - FireEye SUNBURST countermeasures (Snort / Yara / ClamAV rules + IOCs#infosec #CyberSecurity
This from FireEye is an amazing forensics brief. https://t.co/S8EuXAeafy
— richiecook (@richiecook) December 15, 2020
Researchers at @oscontext say the first traffic they saw to the malware controllers in the SolarWinds infrastructure was on 4/4/2020. Fireeye said the malware was config'd to sleep for 2 weeks post-install. Suggests first targets were hit sometime in March https://t.co/Hl6vxHKXD6
— briankrebs (@briankrebs) December 14, 2020
#CyberAttacks: Highly Evasive #Attacker Leverages #SolarWinds Supply Chain With #SUNBURST #Backdoor - https://t.co/HiqX9vhwsO@FireEye
— ????????? ??????? ֎ (@Totocellux) December 14, 2020
?#Enterprises #Organizations#InfoSec #NetworkSecurity#UNC2452 #CyberSecurity#DomainGenerationAlgorithm#LateralMovements#Steganography pic.twitter.com/prdgZvzEyr
Fantastic report by FireEye on the SolarWinds supply chain compromise into organizations around the community including the FireEye intrusion: https://t.co/T950NURayy great insights for defenders to go burn the adversary’s efforts to the ground
— Robert M. Lee (@RobertMLee) December 14, 2020
Solar Winds is widely used in IT, it is systems management software ( monitoring, reporting, patching ), their Orion software was compromised at the source and when they sent out updates ended up exposing lots of customers https://t.co/gkZGvRXwbQ
— Mike Bourne (@bourne0513) December 15, 2020
One of the best reads so far and it’s from FireEye:https://t.co/S8EuXAeafy
— richiecook (@richiecook) December 14, 2020
SUNBURST supply chain attack trojanizing SolarWinds Orion business software updates in order to distribute malware
— File411 (@File411) December 14, 2020
Steganography
“benign XML related to .NET assemblies...actually spread across the many GUID and HEX strings present”
ht @CelerySorbet https://t.co/YluJ9Jyuxr
My heart goes out to all the sysadmins, consultants, MSP’s and it pro’s, that in the upcoming weeks needs to : unplug and reinstall all devices, reset all passwords and re-harden the ad. It’s a lot of work :( if a pandemic wasn’t enough. ?https://t.co/UcsdMKr3Gp
— STÖK ✌️ (@stokfredrik) December 14, 2020
8. Last night the federal Cybersecurity and Infrastructure Security Agency (CISA) issued a rare Emergency Directive 21-01, in response to this KNOWN COMPROMISE involving #SolarWinds Orion products. https://t.co/fmx9TwHH58
— DocRock1007 ?? (@DocRock1007) December 15, 2020
DHSの命令。ソーラーウィンドのオリオンで政府のシステムにハッキングがあったので対応する命令を見たい人はこちら。https://t.co/nkOCgVSJWi
— アーロン大塚 (@AaronOtsuka) December 14, 2020
I’m not a cyber sec expert - these are my layperson concerns
— File411 (@File411) December 14, 2020
->17+ hours & our Govt doesn’t know the scope?
< really dumb that DJT fired CISA’s 1-3 leaders
-this is going to make the OPM breach look infinitesimally basic
Has the DJT Admin given ANY MTTR?https://t.co/rcFoDRnVVF pic.twitter.com/oldhqHhWJI
I’m spitballing here (so you can disagree and/or be skeptical) this attack was/is (it is STILL ongoing) is unlike anything we‘ve seen. I’m thinking a Frankenstein-ish malware
— File411 (@File411) December 14, 2020
CISA Emergency Directive 21-01
“Mitigate SolarWinds Orion Code Compromise”https://t.co/rcFoDRnVVF
CISA has also issued an emergency directive last night with instructions on how to detect and analyze compromised systemshttps://t.co/VkWU6rGTR2 pic.twitter.com/eZOE8gDnxV
— Catalin Cimpanu (@campuscodi) December 14, 2020
Follow up: Here is the Fed Emergency Directive, if you were running SolarWinds Orion you should follow it even as a private sector org. https://t.co/IS6SG8NzIJ #starburst #solarwinds
— Keith Crawford (@tsudo) December 14, 2020
.@CISAgov has issued an emergency directive on actions that gov agencies need to take immediately to mitigate against the SolarWinds threat: https://t.co/WoiLDTCUXu pic.twitter.com/pKdCGr1OK5
— Kim Zetter (@KimZetter) December 14, 2020
There's a lot who thought they were getting a break around the holidays who now aren't. DHS directive on the @solarwinds hack is to pretty much rebuild everything, only after cleaning up the source of the mess. The implications of this hack are huge. https://t.co/oU2VfjSTij pic.twitter.com/FpvUuMxjzU
— Jordan Martin (@bcjordo) December 14, 2020
That certainly looks I pretty good theory given some of the information in DHS notice...https://t.co/DvRaHiFR83
— Gaucho Econ (@superdaveozie) December 14, 2020
There's a lot of folks that want to get into cybersecurity.
— JohnMB | CyberInsight on YouTube (@JBizzle703) December 14, 2020
Right now we have a very large hack w/ supply chain attack (implementing bad code without a vendor knowing).
This is a great learning opportunity/use case to follow.https://t.co/u0FPMObfH1https://t.co/Awnha1z6hR
Not a fun day in the government IT world. https://t.co/Nj61t718Jz
— Patrick Marsh (@pmarshwx) December 14, 2020
Shares of SolarWinds getting clobbered. https://t.co/Ux6MxN5BqW $SWI pic.twitter.com/hcoDIQJEej
— Joe Weisenthal (@TheStalwart) December 14, 2020
U.S. Agencies Hit in Attack by Suspected Russian Hackers https://t.co/vjCTPBiCVf
— Jeffrey Levin (@jilevin) December 14, 2020
Dear FinCEN, did you just deliver my personal transaction history to the Russian government? Thanks for that. Really appreciate this privacy violation.https://t.co/UAZo75nDpE
— Andy Edstrom, Hard Money Zealot (@edstromandrew) December 14, 2020
米 #CISA は政府、民間を問わず、SolarWinds の Orion ネットワーク監視製品群を直ちに使用停止するよう指示。製品を使用している組織に 国務省、CDD、FBI も含まれる。 #脆弱性 https://t.co/ErdMUDDUDk
— OTTOTO (@ottoto2017) December 14, 2020
Suspected Russian hackers spied on U.S. Treasury emails. A must-read for everyone who still believes that backdoors would be a good idea! Here's our view on why we must never allow encryption backdoors: https://t.co/HFT7SqNjJLhttps://t.co/OKq4Y2NscK
— Tutanota (@TutanotaTeam) December 14, 2020
.png)