Before China imprisoned hundreds of thousands of Uighurs, it tried to hack them. https://t.co/m01QKUbFHO
— Carlos Tejada (@CRTejada) July 1, 2020
A new report revealed a Chinese hacking campaign that targeted Muslims beginning as early as 2013 and continues to this day. It shows the lengths to which China’s minders were determined to follow Uighurs as they fled China for as many as 15 countries. https://t.co/mh41EtFiPf
— The New York Times (@nytimes) July 1, 2020
From another discontented borderland...new research shows long before Xinjiang was covered in cameras, Chinese hackers built huge amounts of malware targeting Uighurs. Beginning in 2015, the campaign shows hacking was an early cornerstone of surveillance. https://t.co/ri9OPgGBvb
— Paul Mozur 孟建国 (@paulmozur) July 1, 2020
And what do Chinese-controlled companies do when the U.S. threatens sanctions due to their roles in “demographic genocide?" They hire former U.S. Congressmembers to sway the White House & Senate: https://t.co/YdSAqI76cW https://t.co/4tC0z6f6qP
— Noah Pransky (@noahpransky) July 1, 2020
New research from the security firm Lookout details both the extent and sophistication of a Chinese hacking campaign targeting Uighurs around the world https://t.co/bgYKe5Hh9A
— NYTimes Tech (@nytimestech) July 1, 2020
“Wherever China’s Uighurs are going, however far they go, whether it was Turkey, Indonesia or Syria, the malware followed them there. It was like watching a predator stalk its prey throughout the world.”https://t.co/Wm3O58Ga25
— Theresa Fallon (@TheresaAFallon) July 1, 2020
Chinese government hackers have been installing eight types of malware on the phones of Uighur Muslims going back at least to 2013. Now Beijing's surveillance state also collects Uighur blood samples, voice prints, facial scans and other personal data.https://t.co/RAHJ9Y9ogK pic.twitter.com/Ms6yj8rFPP
— Kenneth Roth (@KenRoth) July 1, 2020
“The tools the hackers assembled hid in special keyboards used by Uighurs and disguised themselves as commonly used apps in third-party websites. Some could remotely turn on a phone’s microphone, record calls or export photos, phone locations and conversations on chat apps.” https://t.co/ED7EVzk72C
— Sui-Lee Wee 黄瑞黎 (@suilee) July 1, 2020
Researchers @Lookout uncovered an #Android surveillance campaign that uses three never-before-seen #spyware tools: SilkBean, GoldenEagle,and CarbonSteal.https://t.co/sRmPEQlupH
— Lindsey O'Donnell Welch (@LindseyOD123) July 1, 2020
Lookout threat researchers have discovered Chinese surveillance campaigns targeting the Uyghur ethnic minority. Activity of these campaigns were observed as far back as 2013. Read our research blog to find out more. https://t.co/RwpdvsbZPR pic.twitter.com/fCVanC7mQ2
— Lookout (@Lookout) July 1, 2020
.@Lookout Threat Intelligence team has discovered four #Android surveillanceware tools. These #malware tools are elements of much larger mAPT campaigns originating in #China, and primarily targeting the #Uyghur ethnic minority. ?
— Ersin Çahmutoğlu (@ersincmt) July 1, 2020
https://t.co/aVdZCuTDSG #apt #surveillance
authoritarian governments will use whatever surveillance tools are at their disposal https://t.co/Ut8nsNGgeW
— Neeraj K. Agrawal (@NeerajKA) July 1, 2020
Fuck China. https://t.co/cH3wWP74Pr
— Khabir (@KhabirM) July 1, 2020
China’s Software Stalked Uighurs Earlier and More Widely, Researchers Learn.
— 3rdkneeblog-joe (@AvroArrowflys) July 1, 2020
Since 2013.
Why has China taken such a hard line against them and really against any religion tied back to Abraham?@thespybrief
https://t.co/anlfOIIjIY
I've been waiting a while for this.
— KDR (@kristindelrosso) July 1, 2020
After years of research with some of the best and brightest coworkers, our findings on novel Android surveillance families as part of long running campaigns targeting the Uyghurs was reported on by the NYT.https://t.co/1NHSNVSYlS
China’s Software Stalked Uighurs Earlier and More Widely, Researchers Learn - The New York Times https://t.co/cCBesjQFpM
— profdeibert (@RonDeibert) July 1, 2020
And now China sinks even lower in its underhanded behaviours ..... https://t.co/wKGOOrrVYz
— Margaret McCuaig-Johnston (@M_Johnston1) July 1, 2020
The surveillanceware our researchers found show that mobile threats are getting sophisticated. What might be today’s advanced attacks will likely become tomorrow’s commercial kit.
— Lookout (@Lookout) July 1, 2020
Read this @nytimes article to find out what our threat team discovered. https://t.co/Z78DHVQ3Gl
A new report revealed a broad campaign that targeted Muslims in China and their diaspora in other countries, beginning as early as 2013.
— Mohammad Farooq (@MohammadFarooq_) July 1, 2020
https://t.co/km2e3XbvIX
“Wherever China’s Uighurs are going, however far they go, whether it was Turkey, Indonesia or Syria, the malware followed them there. It was like watching a predator stalk its prey throughout the world.”https://t.co/Wm3O58Ga25
— Theresa Fallon (@TheresaAFallon) July 1, 2020
"The Chinese hacking campaign, which [...] had begun in earnest as far back as 2013 and continues to this day, was part of a broad but often invisible effort to pull in data from the devices that know people best: their smartphones."https://t.co/x6O6NKJ2UW
— Dino A. Dai Zovi (@dinodaizovi) July 1, 2020
China’s hacking campaigns are not new. World is waking up!
— Subuhi Khan (@SubuhiKhan01) July 1, 2020
https://t.co/Vaqpqe3xsO
“Wherever #China’s #Uyghurs are going, however far they go, whether it was Turkey, Indonesia or Syria, the malware followed them there...It was like watching a predator stalk its prey throughout the world.” -- Apurva Kumar @abby_kcs @hrw @hrw_chinese https://t.co/NEQ62GMgYd
— Sophie Richardson (@SophieHRW) July 1, 2020
China’s Software Stalked #Uighurs Earlier and More Widely, Researchers Learn https://t.co/1aoJY3SB5C (@paulmozur/@nicoleperlroth)
— Greg Walton (@meta_lab) July 1, 2020
“That could be an interesting coincidence,” Mr. Hebeisen said, “or it could be the smoking gun.” #mAPT https://t.co/yGBB0bVeNw
New Android Spyware Tools Emerge in Widespread Surveillance Campaign
— Fabrizio Bustamante (@Fabriziobustama) July 1, 2020
By @threatpost https://t.co/kIg9UjCcH8#CyberSecurity #Hackers #Spyware #IoTSecurity #IoT
Cc: @archonsec @_SChmielewski @PVynckier @Ym78200 @Corix_JC @CioAmaro @AshokNellikar @gvalan @KaiGrunwitz @DrJDrooghaag pic.twitter.com/REVTFeLFOf
New Android Spyware Tools Emerge in Widespread Surveillance Campaign: https://t.co/r06v4h9avA
— The Cyber Security Hub™ (@TheCyberSecHub) July 1, 2020
Here's our blog and full report: https://t.co/UChCH6X7rP
— apurva (@abby_kcs) July 1, 2020
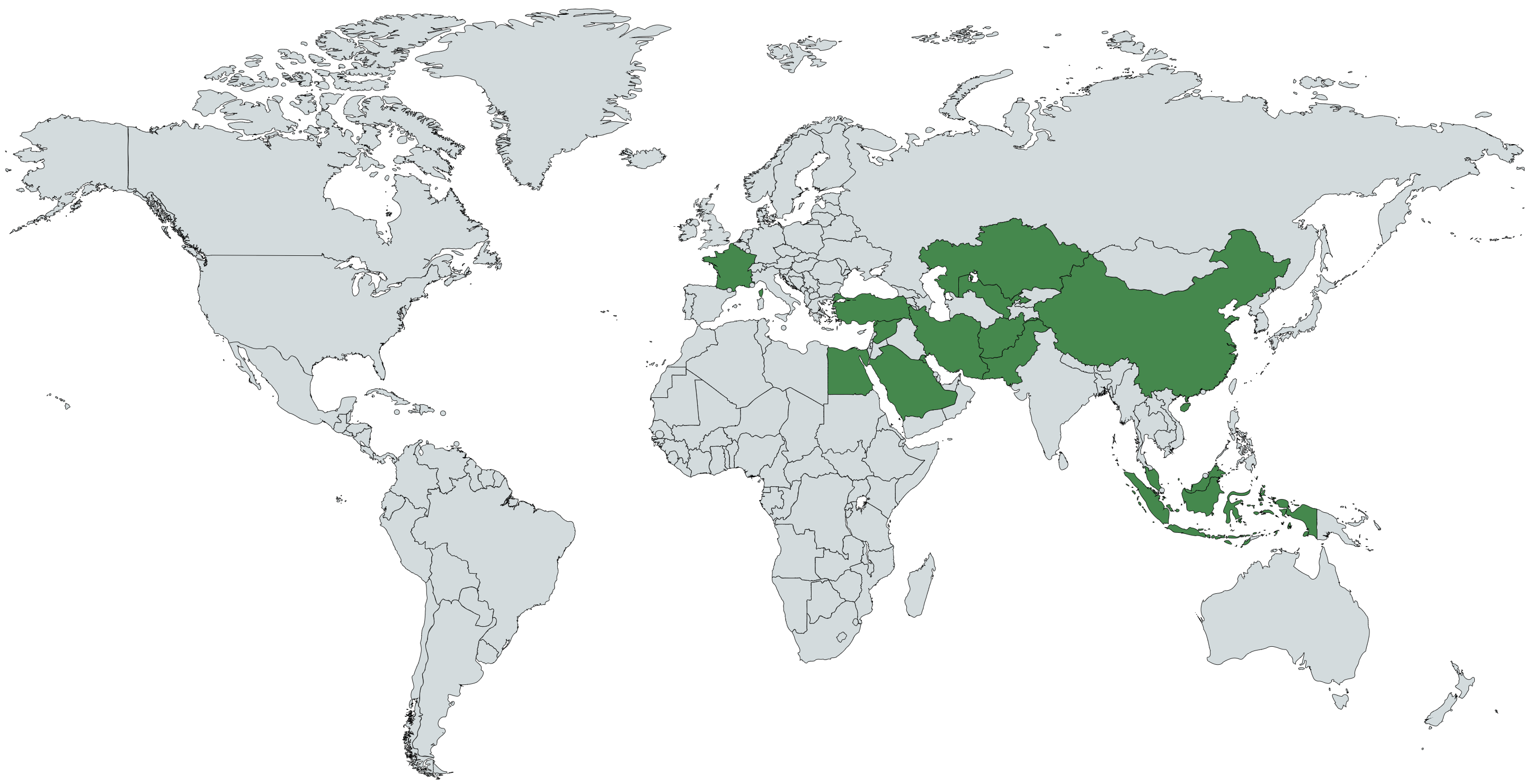
『Our research found that at least 14 different countries may be affected by the campaigns. 12 of these are on the Chinese government’s official list of “26 Sensitive Countries,”』#APT15
— Autumn Good (@autumn_good_35) July 1, 2020
Multiyear Surveillance Campaigns Discovered Targeting Uyghurshttps://t.co/eBH7OJLL6N pic.twitter.com/tkq2oLqlan
Often overlooked but highlighted in this report is the way diaspora populations abroad, including refugees, are targeted by autocrats. https://t.co/VwjFbKXTzh pic.twitter.com/Ph63Iy6lJh
— profdeibert (@RonDeibert) July 1, 2020
The @nytimes reports on the various ways the Chinese government has attempted to spy on #Uyghur activists and the Uyghur diaspora community through a hacking campaign, malicious software and spyware.https://t.co/nQtQcJqDwk
— WorldUyghurCongress (@UyghurCongress) July 2, 2020
China’s persecution of the Uyghur people has been ongoing for years.https://t.co/8Z6quk3PlY
— Drew Pavlou 柏乐志 (@DrewPavlou) July 2, 2020
China’s Software Stalked Ethnic Minorities in China and Around the World, as early as 2013. https://t.co/aTkse4iJ8s
— Michael Ron Bowling (@mrbcyber) July 1, 2020
#CCP_is_terrorist regime China’s Software Stalked Uighurs Earlier and More Widely, Researchers Learn https://t.co/526lN5RSpf
— Jack Maxey (@JackMaxey1) July 1, 2020
A new report revealed a broad campaign that targeted Muslims in #China and their diaspora in other countries, beginning as early as 2013.
— Satyam Shivam (@AazaadSatyam) July 1, 2020
Now where is OIC and it's participants ?
China showed middle finger to you !#1stJuly @JackPosobiec @DVATW https://t.co/Ok4UggXpYj
“Wherever China’s Uighurs are going, however far they go, whether it was Turkey, Indonesia, or Syria, the malware followed them there. It was like watching a predator stalk its prey throughout the world.” https://t.co/ti8sGJuMG0
— Rowaida Abdelaziz (@Rowaida_Abdel) July 1, 2020
Before the Chinese police hung high-powered surveillance cameras and locked up ethnic minorities by the hundreds of thousands in China’s western region of Xinjiang, China’s hackers went to work building malware, researchers say. https://t.co/fROx0LT5vr
— PEN America (@PENamerica) July 1, 2020
.png)