These kind of attacks are getting more common, they will explode with growing crypto value: https://t.co/PzS8tg1HWi@KomodoPlatform wallets, like upcoming atomicdex, are now among the most hardened & secure of this space since lessons of last year attack have been taken seriously
— Mr.KomodoWorld (@MrKomodoWorld) April 18, 2020
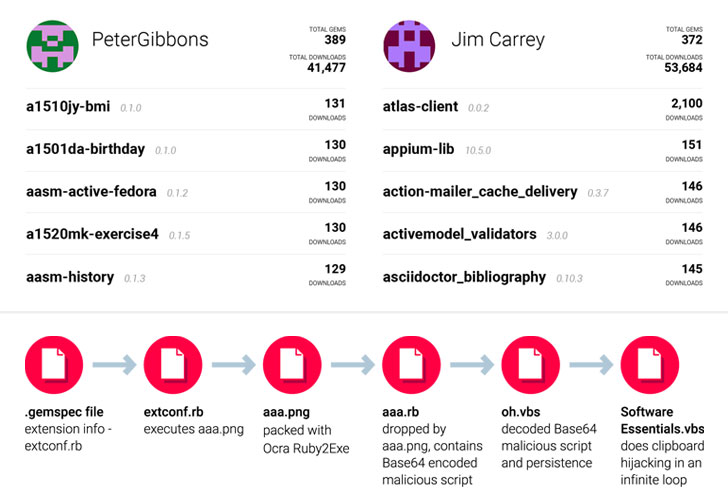
* 760 malicious RubyGems published in February from two accounts
— Maya Kaczorowski (@MayaKaczorowski) April 18, 2020
* typosquatting attack - "atlas-client" swapped underscore for dash succesfully
* malware captures clipboard data, looks for bitcoin addresses to redirect, tries to establish persistencehttps://t.co/Yg6ui2pxqs
More terrifying software supply chain security attacks https://t.co/1dEznem3oa
— Dino A. Dai Zovi (@dinodaizovi) April 18, 2020
Hackers typo-squatted 725 popular Ruby libraries. When the victim installs the malware, it sets up a clipboard hijacker that tries to steal bitcoin. https://t.co/k2PfdpD5bd
— Ben Sandofsky (@sandofsky) April 17, 2020
Clipboard hijacking malware found in 725 Ruby libraries
— Catalin Cimpanu (@campuscodi) April 17, 2020
- Libraries uploaded on RubyGems between Feb 16 and 25
- Removed on Feb 27
- Malware would replace BTC addresses in the Windows clipboard to hijack BTC paymentshttps://t.co/mKo2XnOTDF pic.twitter.com/g7y40X34Zn
Hackers use typosquatting to trojanize 700 libraries in Ruby Repository #CyberSec #Security #ThreatIntel #cybersecurity #dataprotection #privacy #cyberthreats #hackers #cybercrime #darkweb #digitalrisk #databreaches #cyberintelligence https://t.co/nDsm4yUUoL
— Javier Carriazo (@javier_carriazo) April 18, 2020
Over 700 Malicious Typosquatted Libraries Found On RubyGems Repository #CyberSec #Security #ThreatIntel #cybersecurity #dataprotection #privacy #cyberthreats #hackers #cybercrime #darkweb #digitalrisk #cyberintelligence https://t.co/qshjuU4yVG
— Javier Carriazo (@javier_carriazo) April 17, 2020
WARNING: To target #software developers, supply chain attackers recently caught distributing over 700 malicious libraries—written in Ruby #programming language—through the official RubyGems repository using #typosquatting gems.
— Swati Khandelwal (@Swati_THN) April 16, 2020
Details ➤ https://t.co/JZpPKkCQKk#cybersecurity
Over 700 Malicious Typosquatted Libraries Found On RubyGems Repository https://t.co/j1rxc1KPiD
— Nicolas Krassas (@Dinosn) April 16, 2020
* 760 malicious RubyGems published in February from two accounts
— Maya Kaczorowski (@MayaKaczorowski) April 18, 2020
* typosquatting attack - "atlas-client" swapped underscore for dash succesfully
* malware captures clipboard data, looks for bitcoin addresses to redirect, tries to establish persistencehttps://t.co/Yg6ui2pxqs
Mining for malicious Ruby gems https://t.co/qmXpJ8DqiA pic.twitter.com/u7LVf3q4Ru
— Hiroshi SHIBATA (@hsbt) April 17, 2020
ℹ️ Typosquatting:
— Karsten Hahn (@struppigel) April 17, 2020
"threat actors intentionally name malicious packages to resemble the popular ones [...] in hopes that an unsuspecting user will mistype the name and [...] install the malicious package"
About finding typosquatting RubyGems ⬇️https://t.co/rwUXm9rC44
This is why @bc_vault #bcvault #cryptowallet has BIG SCREEN! It is of utter importance to always check crypto addresses you are sending money to! Good luck with “Tiny screen” devices...https://t.co/hGbmCmJMlq
— Alen Salamun (@AlenSalamun) April 17, 2020
Clipboard hijacking malware found in 725 Ruby libraries. https://t.co/AuvZibTI2j #Malware #ruby #CyberSecurity
— Shieldly (@shieldly) April 17, 2020
The malware would replace Bitcoin addresses copied to the clipboard with one controlled by the attacker. #dynamiccio #linux #girlswhocode #tech @rneelmani @hacback17https://t.co/3kEL5jAAWI
— Dynamic CIO (@DynamicCIO) April 17, 2020
These kind of attacks are getting more common, they will explode with growing crypto value: https://t.co/PzS8tg1HWi@KomodoPlatform wallets, like upcoming atomicdex, are now among the most hardened & secure of this space since lessons of last year attack have been taken seriously
— Mr.KomodoWorld (@MrKomodoWorld) April 18, 2020
Supply-chain attack hits RubyGems repository with 725 malicious packages https://t.co/xAOLhfD2o5
— Christopher Parsons (@caparsons) April 17, 2020
— Brando (@_branzo_) April 18, 2020
Almost every programming language of woahfully unprepared to deal with supply chain attacks.
— ¯\_(ツ)_/¯ (@SeanTAllen) April 17, 2020
Package repositories plus complete trust in modules and ambient authority everywhere is a fucking disaster.https://t.co/t6thVcg21O
Over 700 Malicious Typosquatted Libraries Found On RubyGems Repository #ruby #rails https://t.co/QygPMjK2kM
— Rails Links (@railslinks) April 18, 2020
"Over 700 Malicious Typosquatted Libraries Found On RubyGems Repository". Elm tackles this kind of issue by requiring all packages to consist of pure functions. All effects have to be wired in explicitly in application code. https://t.co/z0vFwqRrbr #elmlang
— Alex Korban (@alexkorban) April 18, 2020
Over 700 malicious RubyGems packages were uploaded between February 16 and February 25. Most of them had the capability to steal cryptocurrency by replacing the wallet address on the clipboard to the attacker's wallet address. https://t.co/JZccp64dZr#Infosec
— John Opdenakker - Lockdown counter: 33 (@j_opdenakker) April 18, 2020
Researchers from @reversinglabs discover #malware pre-packaged in #RubyGems repositories designed to replace #Bitcoin addresses with the #BTC address of the attacker. #infosec #Cybersecurity #DFIR #cybercrime #CISO #IOC #crypto #SupplyChain https://t.co/3jfVrL8Ozg
— Brent Muir (@bsmuir) April 19, 2020
Alternative headlines for the supply-chain "attack" on RubyGems repository https://t.co/hibOvvQKVj
— Christian Heimes (@ChristianHeimes) April 18, 2020
"Malicious content found on the internet"
"Chrome downloads Trojan horse after user clicks on link"
"curl doesn't block latest virus"
"PyPI and NPM contain badly written stuff"
“There are very few protections out there for software developers to make sure that packages they install from these repositories are malware free…There is a huge gap in the market at the moment which is being exploited by malware authors.” https://t.co/7Lvp77lno8
— Christopher Allen (@ChristopherA) April 19, 2020
.png)